Mainframe Discovery and Protection Solution: Security for Critical z/OS Data
PKWARE provides enterprise-wide discovery of z/OS applications and critical data elements to enable compliance and modernization. Backed by four decades of mainframe expertise and IBM Partner Plus status, we’re a proven leader in solving complex z/OS data security challenges.

Trusted By Leading Organizations for Over 40 Years
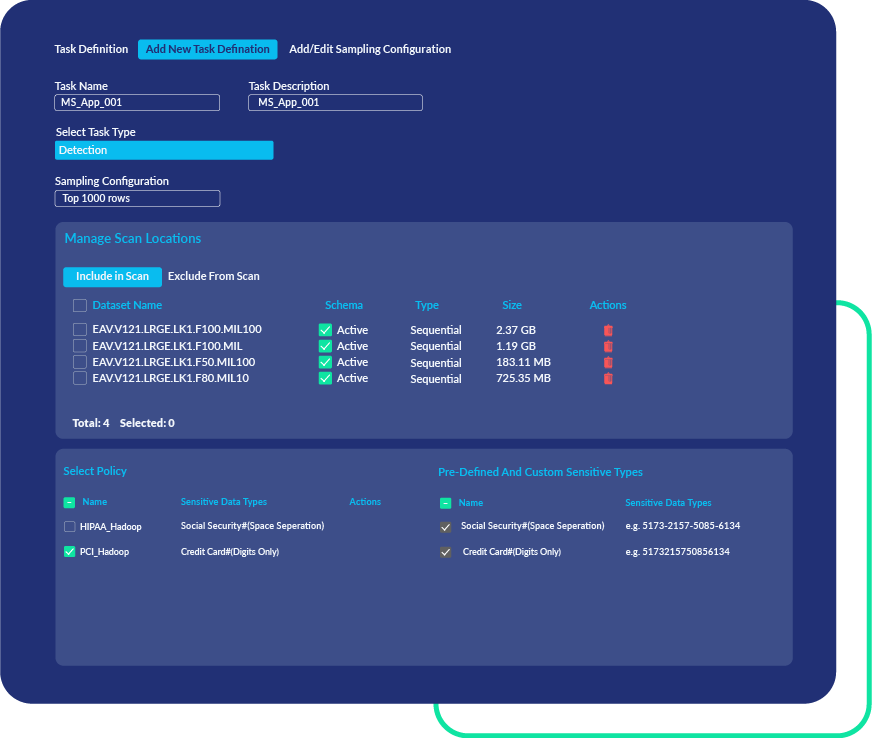
Gain Comprehensive Visibility of z/OS Application Datasets
Organizations running on IBM z/OS often struggle to identify where sensitive data resides and how it’s used as it moves beyond the mainframe. This lack of visibility creates compliance challenges and security risks. PK Protect solves this by delivering discovery of application data, critical data elements, and processes. Discovery, paired with persistent encryption, simplifies regulatory compliance, reduces risk, and accelerates modernization.
Why PK Protect for z/OS

Uncover Risks and Ensure Compliance
When mainframe data leaves z/OS, organizations lose track of where sensitive information exists, leading to security and compliance gaps. Our mainframe data security platform reveals these exposure risks with application and critical data element discovery so you can meet mandates and avoid fines for noncompliance. It also accelerates SBOM (software bill of materials) creation, saving time during audits and delivering insights into sensitive elements and application components.

Prevent Data Leakage and Enforce Governance
PK Protect provides application discovery and encryption to proactively prevent data exposure, at rest and in motion. It enables persistent encryption for data moving in and out of z/OS, de-identifies production data for safe use in lower environments, and secures sensitive information before it enters AI models, ensuring governance and minimizing risk across the data lifecycle.

Support Application Modernization and Cloud Migration
Most organizations on the mainframe are modernizing workloads on z/OS or integrating them with the cloud, rather than moving off the platform. Our mainframe discovery solution supports this by scanning and harvesting mainframe metadata, preventing exposure during cloud migrations. It also maps legacy data to compliant cloud storage structures. This ensures sensitive data remains protected, simplifies audits, and strengthens long-term governance.







