Protect Your Data Today. Stay Resilient Tomorrow.
Quantum computing is advancing at a “doubly exponential” rate, as described by Neven’s Law. This rapid progress means traditional encryption methods will soon be at risk. To remain secure, organizations must adapt to new standards. PKWARE enables businesses to achieve crypto agility and mitigate emerging threats.
Crypto Agility with PKWARE
We’ve simplified the complex, resource-intensive process of transitioning to quantum-safe encryption with PK Protect.
PKWARE Quantum Readiness Assessment
Our Quantum Readiness Assessment (QRA) helps organizations understand what data is currently encrypted and puts a plan in place to continue to protect data as quantum computing evolves. Explore what’s included in the QRA.

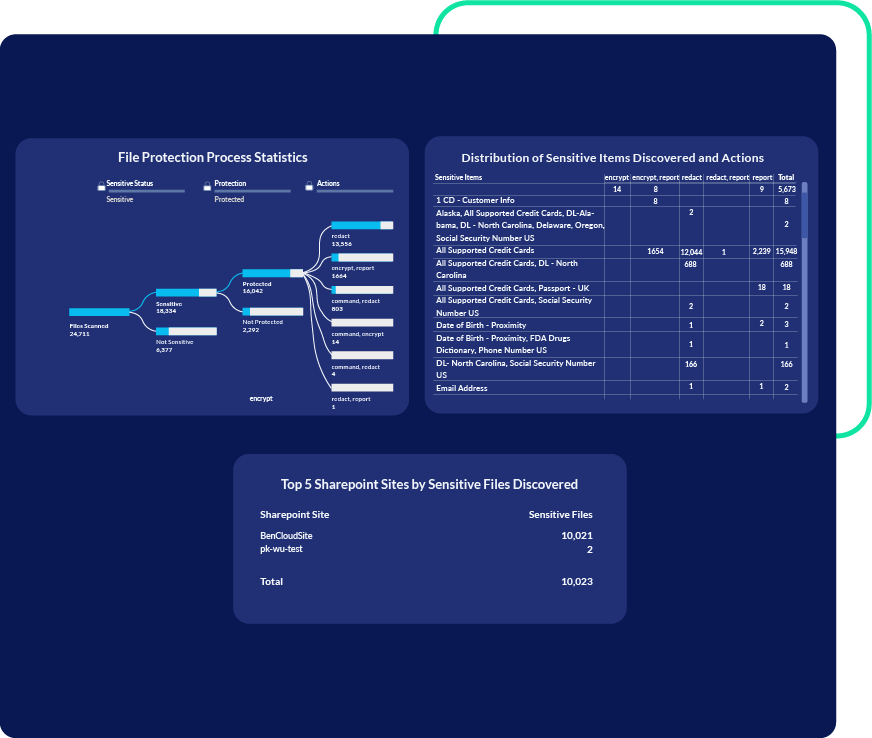
Encryption Discovery Report
Encryption discovery scans give you clear visibility into your risk footprint. We provide a detailed report that pinpoints encrypted file hot spots, encryption actions by users, and files with outdated encryption standards.
Remediation Recommendations
The QRA includes actionable guidance based on findings to reduce risk and strengthen security. Recommendations may include quarantining, deleting, or redacting encrypted files, based on the file content or last accessed and modified dates.








