Protection That Doesn’t Impact Users
Secure data exchange with partners, contractors, vendors, and customers is critical to operations. But intrusive security measures hinder users. Some may even work around them, leading to vulnerabilities. PK Protect solves this, establishing secure and compliant data use and sharing that isn’t disruptive.
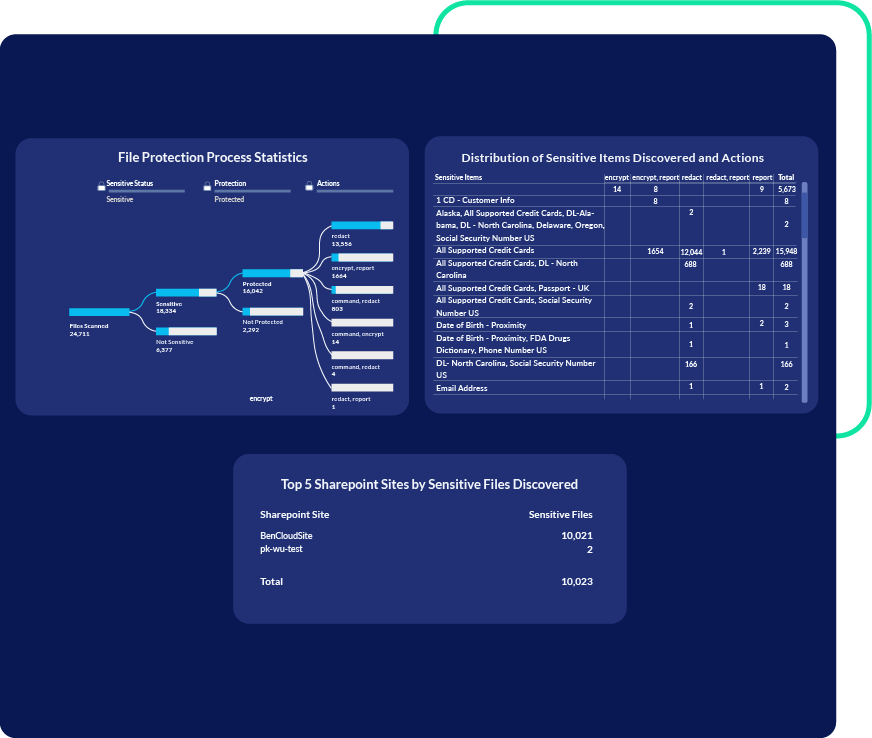
How We Support Security and Productivity
Secure Data Exchange Platform Features

Policy-Based Remediation
Define policies to encrypt, redact, or mask data centrally. Customizable policies ensure rules are applied uniformly across all files and data sources, with different types of remediation for different types of data. Eliminate manual processes and secure data without reliance on user behavior.








