De-Identify Production Data for Safe Development
PK Protect keeps sensitive data secure while maintaining its usability for critical business needs like development and testing. Use it to de-identify data to provide developers with safe datasets.
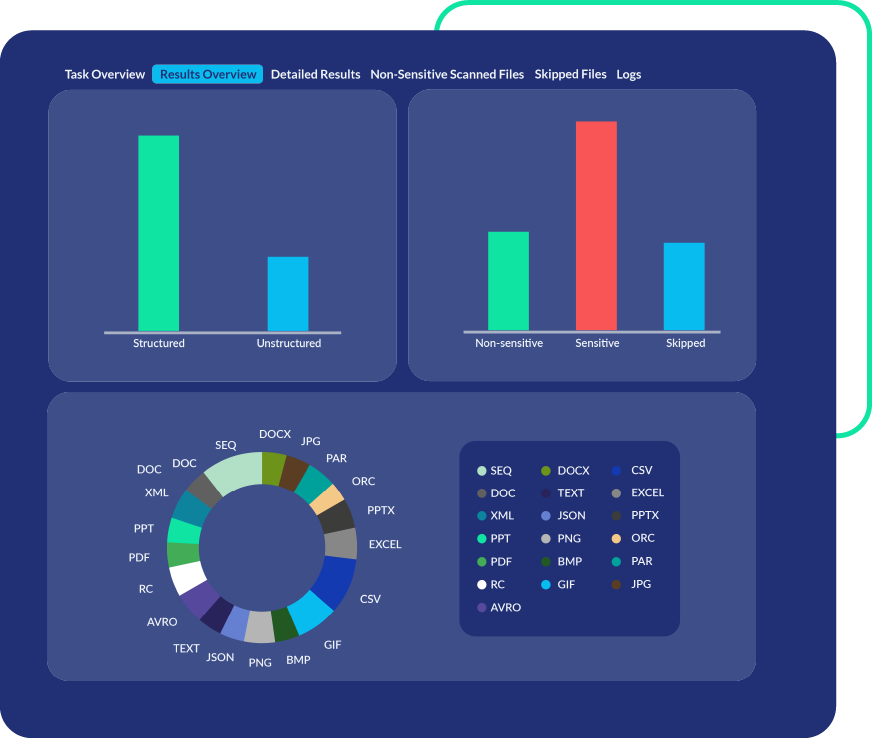
Data Security for Lower-Level Environments
Comprehensive Data Governance

Enterprise-Wide Data De-Identification
PK Protect can de-identify sensitive data across hundreds of platforms. Customers leverage it to secure data on Oracle, SQL Server, Postgres, DB2, Hadoop, AWS, Azure, Snowflake, Salesforce, and more.
Centralized Policies for Consistent Protection
With PK Protect, you can enforce policies uniformly across all repositories to de-identify data. Simplify governance and administration with centralized control.


Referential Integrity in Test Environments
Even after sensitive data is anonymized with PK Protect, relationships between records remain intact. This ensures development and QA datasets behave as they would in production for realistic, secure testing.






