PK Protect for z/OS – The Future of Mainframe Data Protection

You heard it at SHARE, you’ve heard it all over pkware.com, and you’ve likely heard of it from our channel partners. Let’s talk about what, why, where, and how PK Protect for z/OS with SchemaLink Technology works.
What is PK Protect for z/OS?
PK Protect for z/OS with SchemaLink Technology solves the issue of sensitive data duplication, replication, and proliferation. It is one of the most secure methods for managing personally identifiable information (PII), thereby ensuring data privacy and adherence to compliance regulations. In addition to peace of mind, it knows where all of your data lives, inside and outside of your mainframe, and keeps it protected.
“SchemaLink Technology* is an innovative feature within PK Protect for z/OS and offers unparalleled support for z/OS datasets, whether they include copybooks or not. It’s one of the pioneering solutions in the industry that delivers enhanced flexibility and convenience, allowing you to easily safeguard and manage your data, irrespective of the file structure, making PK Protect for z/OS the ultimate solution for comprehensive data security and accessibility. When we developed PK Protect for z/OS it was important to PKWARE that we use YOUR data definitions to read YOUR datasets to provide you with an accurate way to discover and protect sensitive data on z/OS, giving you ultimate control over your most important mainframe data.
Why is revisiting our mainframe data protection strategy so important today?
Mainframe data is arguably some of the most sensitive and critical data generated today. Because they have been entrusted to process extremely sensitive data, such as financial receipts, customer records, and intellectual property, securing this information is the most important service a company can provide to their customers. As reassuring as it is to know you are generating, processing, and storing this data on IBM Z, the journey of protecting this data is just beginning. Remember, there are tens of thousands of professional hackers that want your data, and they only need to be successful once. Your company cannot afford that reputational or financial damage.
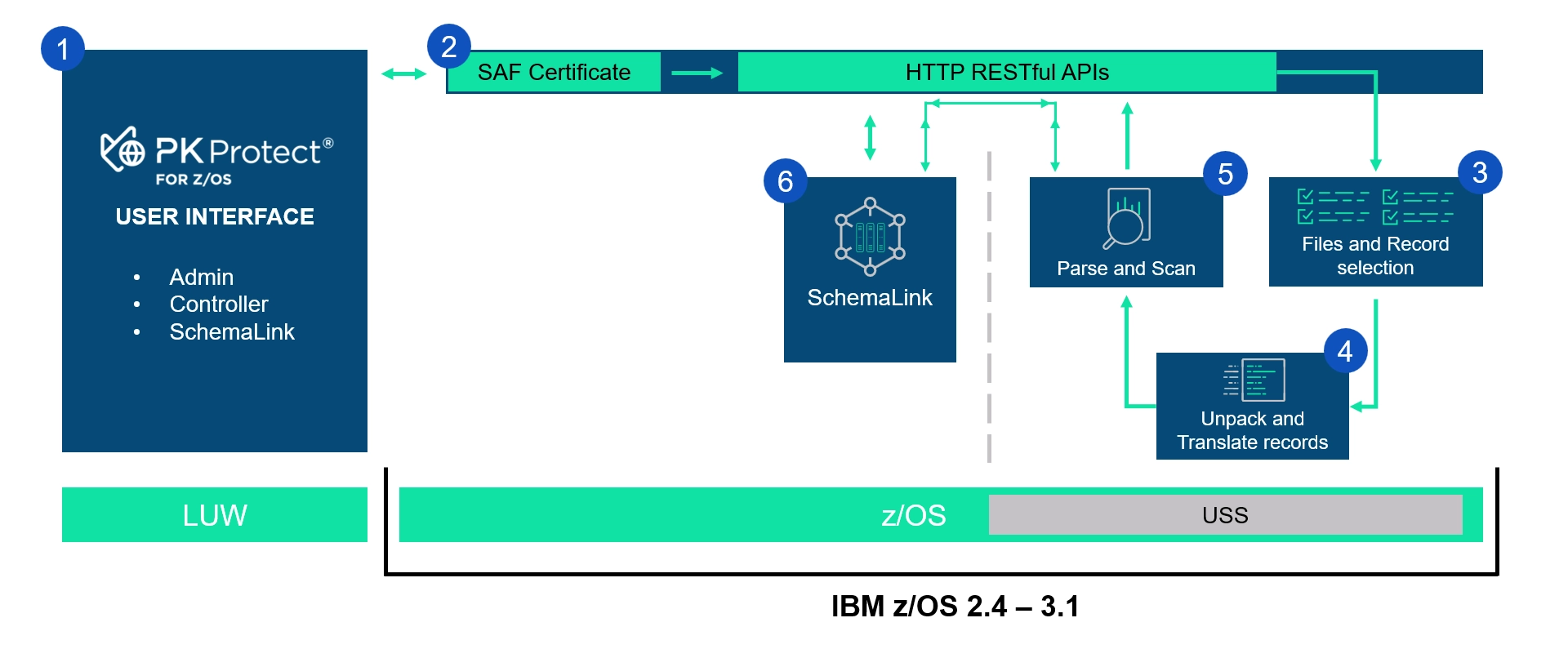
Here's is how it works
- PK Protect for z/OS with SchemaLink technology uses a LUW Java-based GUI for Administrative, Controller, and SchemaLink needs.
- The UI uses SAF-based certificate authentication and HTTP RESTful APIs to communication with the IDP or Intelligent Data Processor that resides in the UNIX System Services. This is where the core of the discovery process takes place.
- The data set discovery request comes from the UI into the Files and Record selection process. This is where sample sizes and policies are applied to the requested data sets.
- The EBCDIC files are unpacked (if decimal data exists), record lengths are adjusted, and data is translated from EBCDIC to ASCII
- The records are sent to be parsed and scanned
- The records are matched against the respective data set schemas stored in the SchemaLink database, and then the scan process can begin.
Use Case: One of the Top Financial Institutions in the US
PKWARE did a risk assessment on 504 million of their VSAM records and uncovered that 88% of the data scanned contained vulnerable sensitive data.
422 million credit card numbers and 450 million social security numbers were found which could potentially have led to approx. $150 million in fines.
Download Solution Overview: PK Protect for z/OS with SchemaLink Technology
Click here to get started today on a data risk assessment with one of our z/OS experts.

You heard it at SHARE, you’ve heard it all over pkware.com, and you’ve likely heard of it from our channel partners. Let’s talk about what, why, where, and how PK Protect for z/OS with SchemaLink Technology works.
What is PK Protect for z/OS?
PK Protect for z/OS with SchemaLink Technology solves the issue of sensitive data duplication, replication, and proliferation. It is one of the most secure methods for managing personally identifiable information (PII), thereby ensuring data privacy and adherence to compliance regulations. In addition to peace of mind, it knows where all of your data lives, inside and outside of your mainframe, and keeps it protected.
“SchemaLink Technology* is an innovative feature within PK Protect for z/OS and offers unparalleled support for z/OS datasets, whether they include copybooks or not. It’s one of the pioneering solutions in the industry that delivers enhanced flexibility and convenience, allowing you to easily safeguard and manage your data, irrespective of the file structure, making PK Protect for z/OS the ultimate solution for comprehensive data security and accessibility. When we developed PK Protect for z/OS it was important to PKWARE that we use YOUR data definitions to read YOUR datasets to provide you with an accurate way to discover and protect sensitive data on z/OS, giving you ultimate control over your most important mainframe data.
Why is revisiting our mainframe data protection strategy so important today?
Mainframe data is arguably some of the most sensitive and critical data generated today. Because they have been entrusted to process extremely sensitive data, such as financial receipts, customer records, and intellectual property, securing this information is the most important service a company can provide to their customers. As reassuring as it is to know you are generating, processing, and storing this data on IBM Z, the journey of protecting this data is just beginning. Remember, there are tens of thousands of professional hackers that want your data, and they only need to be successful once. Your company cannot afford that reputational or financial damage.
Here's is how it works
- PK Protect for z/OS with SchemaLink technology uses a LUW Java-based GUI for Administrative, Controller, and SchemaLink needs.
- The UI uses SAF-based certificate authentication and HTTP RESTful APIs to communication with the IDP or Intelligent Data Processor that resides in the UNIX System Services. This is where the core of the discovery process takes place.
- The data set discovery request comes from the UI into the Files and Record selection process. This is where sample sizes and policies are applied to the requested data sets.
- The EBCDIC files are unpacked (if decimal data exists), record lengths are adjusted, and data is translated from EBCDIC to ASCII
- The records are sent to be parsed and scanned
- The records are matched against the respective data set schemas stored in the SchemaLink database, and then the scan process can begin.

Use Case: One of the Top Financial Institutions in the US
PKWARE did a risk assessment on 504 million of their VSAM records and uncovered that 88% of the data scanned contained vulnerable sensitive data.
422 million credit card numbers and 450 million social security numbers were found which could potentially have led to approx. $150 million in fines.
Download Solution Overview: PK Protect for z/OS with SchemaLink Technology
Click here to get started today on a data risk assessment with one of our z/OS experts.


